Trend Micro securecloud
Hi everyone,
I m going the share with
you my technical knowledge of Trend Micro securecloud. but first let me explain
what this product do. Trend Micro SecureCloud™ provides
distinctive data protection for cloud and virtual environments using
encryption with policy-based key management and unique server validation.
This protection safely and easily secures sensitive data stored with leading
cloud service providers, including Amazon EC2, Dell, Eucalyptus, and NTT
America, as well as VMware vCloud and any virtual environment.
Security
·
Enables data protection in
private and public clouds and virtual environments
·
Promotes safe storage
recycling by rendering any data remnants indecipherable
·
Facilitates compliance and
supports internal governance
Control
·
Specifies when and where
information is accessed through policy-based key management
·
Offers unique server
authentication to ensure only authorized virtual machines receive keys
·
Provides remote management
of cipher keys to enhance data security and control
·
Creates critical separation
of duties between cloud providers and data owners
Choice
·
Deploys as either a hosted
service or as an on-premise software application
·
Enables cloud vendor
changes with customer encryption key ownership
Now let’s get inside the
product, we see this characteristic
Advanced
Security Techniques
• Features
FIPS 140-2 certification and FIPS approved AES encryption
• Encrypts
and decrypts information in real time, so data at rest is always protected
•Applies
whole volume encryption to secure all data, metadata, and associated structures
without impacting application functionality
Access
and Authentication Controls
• Employs
role-based management to help ensure proper separation of duties
•Automates
key release and virtual machine authorization for rapid operations or requires manual
approval for increased security
• Offers
cloud provider credential rotation2
Policy-driven
Key Management
• Uses
identity- and integrity-based policy enforcement to ensure only authorized
virtual
machines receive keys and access secure volumes
•
Integrates with Deep Security Manager to further validate the environment security
posture
• Enables
the use of policies to determine when and where information is accessed
Auditing, Reporting, and Alerting
• Logs
actions in the management console for audit purposes
• Provides
detailed reporting and alerting features with incident-based and intervalbased
notifications
When you
arrive in secure cloud you get the real time matrix of running instance and there
statues with policies
You can get
more information in clicking on the instance and approved or deny is status
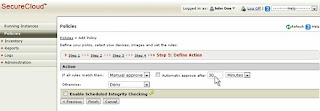
Policies
are easy to make in 5 clicks
You can
specify a policy for each provider or for a group of instance
When a
policy is approuved it is now avalaible inside the cloud provider datacenter,
and it s encrypted.






.JPG)
Commentaires
Publier un commentaire